At Hifen, we take pride in partnering with exceptional clients, guiding them through the complexities of safeguarding their operational landscapes. We’re excited to share insights from a recent initiative where we assisted a Medical Device Manufacturer in bolstering their Operational Technology (OT) security framework and mitigating associated risks using the Purdue Model. OT, often a departure from the familiar terrain of IT security, encompasses specialized devices and systems—some with proprietary hardware, code, and protocols, and often characterized by extended operational lifespans. These components are integral to managing processes, manufacturing systems, climate control, access security, surveillance, and more. Whether isolated or network-connected, whether governed by physical control systems, software, or operated from a centralized server or console, the nuances of OT systems can vary widely. Even the state of firmware—upgraded or outdated—can vary, contingent on the availability of updates or the ongoing support from the original manufacturers.
The integration and strengthening of IT infrastructure inevitably shine a light on the latent vulnerabilities within OT systems. As we fortify IT defenses, the security of OT components becomes increasingly critical, as they might serve as potential gateways for adversaries. Hence, understanding and securing these systems is not just a technical challenge but a strategic imperative to prevent potential breaches. Let’s delve into a structured approach to fortify OT security in the context of a Medical Device Manufacturer, leveraging the Purdue Model to establish robust defenses against the evolving landscape of cyber threats.
Implementing OT Security following the Purdue Model involves establishing a multi-layered defense strategy to protect the integrity, availability, and confidentiality of manufacturing systems and data. The Purdue Model organizes industrial control systems (ICS) architecture into different levels, from the enterprise level to the factory floor, providing a structured approach to securing OT environments.
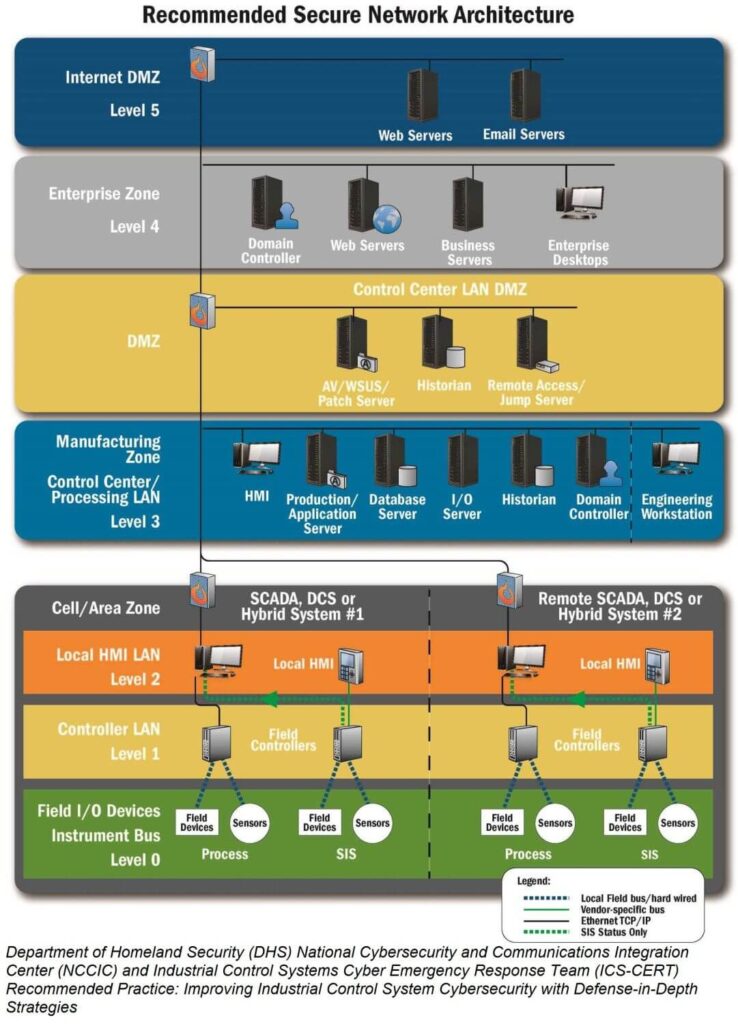
The Purdue Model
First, let’s brief ourselves on the Purdue Model Levels
- Level 0: Physical process (medical device manufacturing equipment).
- Level 1: Intelligent devices (sensors, actuators, and other devices directly interacting with the manufacturing process).
- Level 3: Manufacturing Operations Systems (systems managing production operations, batch management, etc.).
- Level 4: Business Logistics Systems (enterprise resource planning systems, HR, finance).
- Level 5: Enterprise Network (corporate IT network).
The Breakdown
Using that as our basis, here are the things you need to focus on to implement the Purdue model in an engagement, tailored for our Medical Device Manufacturer:
Risk Assessment and Network Segmentation
- Risk Assessment: Conduct a comprehensive risk assessment focusing on OT assets, identifying critical systems, potential vulnerabilities, and threats specific to the medical device manufacturing sector.
- Network Segmentation: Implement network segmentation based on the Purdue Model levels. Use firewalls and demilitarized zones (DMZs) to separate networks, especially distinguishing between OT and IT networks (Level 3.5 is often used for DMZ).
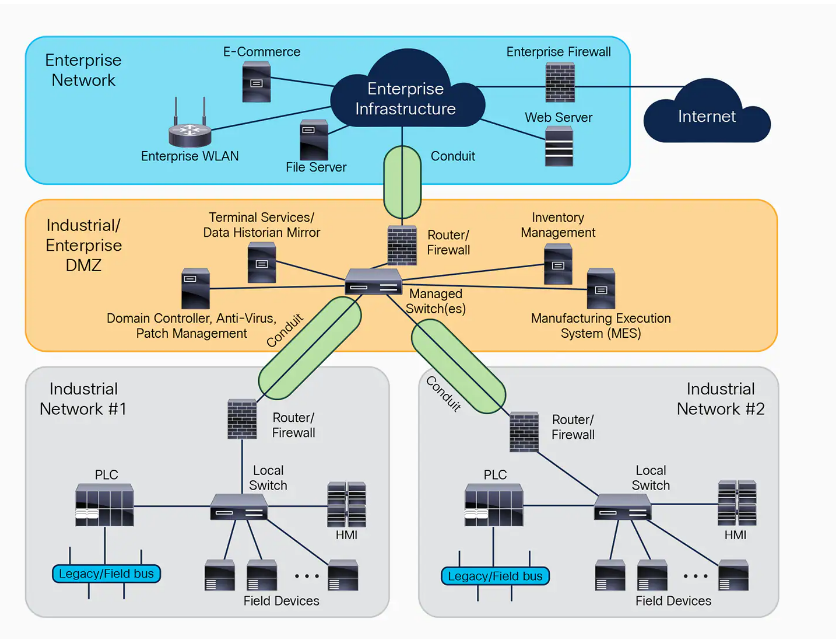
Secure the Control Layer (Levels 0, 1, and 2)
- Device Hardening: Apply security best practices to harden devices, such as disabling unnecessary services, changing default passwords, and applying patches.
- Access Control: Ensure strict access control and authentication mechanisms for devices and systems.
- Network Security: Employ network security measures including firewalls, intrusion detection systems (IDS), and virtual private networks (VPNs) for remote access.
Secure the Operations and Management Layers (Levels 3 and 4)
- Data Protection: Implement data integrity and confidentiality measures, such as encryption for data at rest and in transit, especially for sensitive manufacturing data and intellectual property.
- System Security: Ensure systems are updated and patched. Use antivirus and endpoint detection and response (EDR) solutions.
- Access Management: Utilize role-based access control (RBAC) and enforce the principle of least privilege.
Integrate IT and OT Security Practices (Level 5)
- Collaboration: Foster collaboration between IT and OT teams to ensure security measures are aligned and comprehensive.
- Continuous Monitoring: Implement continuous monitoring of the IT and OT networks for anomalies, breaches, and unauthorized activities.
- Incident Response: Develop and regularly update an incident response plan that includes both IT and OT aspects, ensuring quick containment and mitigation of security incidents.
Compliance and Continuous Improvement
- Compliance: Adhere to regulatory requirements specific to the medical device industry (e.g., FDA guidelines, HIPAA for patient data protection) and cybersecurity standards (e.g., NIST, ISO 27001).
- Training and Awareness: Conduct regular security awareness training for all employees, focusing on the unique aspects of OT security.
- Continuous Improvement: Implement a continuous improvement process for security, regularly reviewing and updating security policies, procedures, and technologies.
Adding the Dash
This is no easy undertaking however. We can assume that discovery and assessment across even one location can take many months if the client has no prior assessments, documentation, or information on their facility. Securing OT environments in a medical device manufacturing context requires a detailed and structured approach, leveraging the Purdue Model for effective segmentation and protection of critical manufacturing systems. This involves a combination of technical controls, policies, procedures, and ongoing collaboration between IT and OT teams, underpinned by a commitment to regulatory compliance and continuous improvement.
If you would like to talk to one of our experts about why you should perform an OT security assessment, or would like more information and assistance in your implementation, please reach out and we will be happy to schedule a call with one of our experts.

